Malware program Emotet and how to check for the infection with EmoCheck
What is Emotet?
Emotet is a malware (virus program) and cybercrime organization detected in 2014 and used as a virus to steal customer data from foreign banks.
In January 2021, the server that was the base of Emotet's operations was taken down in an international collaborative operation by authorities from the Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada, and Ukraine.
With this, the Emotet threat was supposed to have disappeared, but several organizations have confirmed that its activities have resumed around November 2021, and Japanese National Police Agency and JPCERT Coordination Center, a nonprofit organization that works on computer security issues, have alerted the public.
Recently, PayPay announced that it will be taking measures against Emotet, and several news sites featured the announcement. These measures are to delete attachments when a password-protected compressed file or Microsoft Office macro file is received via e-mail.
Emotet search volume in the last 5 years
Worldwide
Japan
*About Google Trends
Google Trends is a tool that visualizes how many searches for a certain word have been conducted on Google.
The number displayed here is not the number of searches.
For example, a value of 100 means that the word has peaked in searches; a value of 50 means that the word has half the search popularity.
A score of 0 means that there was not enough data for this word.
infection route
Emotet is said to be transmitted mainly from Word and Excel files with macros attached to e-mails, or from password-protected Zip files that contain these files.
The infection is said to occur by executing macros in these attachments, but in the past, there have been confirmed cases of infection from links in the body of e-mails.
In addition, although infection from Outlook was previously confirmed, infection via Thunderbird has also been confirmed.
As for operating systems, it seems that most infections are on Windows, but according to an overseas article, infections on Apple devices have also been confirmed in 2019.
See Also : What is Emotet | How to best protect yourself
Impact
Japanese National Police Agency has published the results of its analysis of Emotet and on June 9, 2022, published a new impact.
According to the report, Emotet infection can cause the following damage.
Once infected with Emotet, the following damage may occur
- Passwords and other information recorded in e-mail software and browsers are stolen.
- The body text of past e-mails, e-mail addresses, etc. are stolen.
- Stolen email-related information is exploited to send emails intended to spread the infection.
- The infection spreads to other computers in the network.
- Infected by other malware (e.g., malware designed to steal Internet banking information).
- Credit card information stored in the browser is stolen.
Translated from : 「Results of Emotet's analysis | Japanese National Police Agency @police」(Official website of Japanese National Police Agency)
The last, "Credit card information stored in your browser is stolen." was added on June 9.
It has been discovered that credit card information stored in Google's Chrome web browser has been stolen and may be known to third parties.
How to check if you are infected
You can check to see if your computer is infected with Emotet by using EmoCheck, a free program published by the JPCERT Coordination Center, a non-profit organization that investigates and addresses computer security issues. EmoCheck is a free program published by the JPCERT Coordination Center.
EmoCheck is available on the company's GitHub and can be downloaded from there.
It is recommended to download the latest version of EmoCheck.
EmoCheck's GitHub
Releases · JPCERTCC/EmoCheck · GitHub
Instructions for use are summarized in the README below.
Japanese README
EmoCheck/README_ja.md at master · JPCERTCC/EmoCheck · GitHub
English README
EmoCheck/README.md at master · JPCERTCC/EmoCheck · GitHub
Japanese National Police Agency has also published a document explaining how to use it.
How to run EmoCheck, a tool to check for Emotet infection
This program is a command line program. Analysis begins by double-clicking the downloaded exe file, and the results are displayed when finished.
The results are also saved in a text file format in the directory where the program was downloaded.
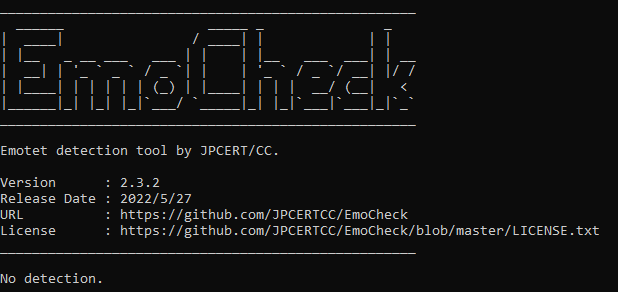
The EmoCheck execution screen, displayed in Japanese if the language setting of the PC is Japanese.
If infection is confirmed
The JPCERT Coordination Center has published an FAQ on how to handle the problem.
How to Respond to Emotet Infection (FAQ) - JPCERT/CC Eyes | JPCERT Coordination Center official Blog
If you belong to an organization, ask the computer-related department for advice.
